Edge Node and Device Protection
Xiid SealedTunnel™ 4.0 Case Study
Edge Device Security is Critical
As companies continue to extend the boundaries of their networks to IoT devices, sensors, and workers in a distributed workforce, it is critical to ensure that communications to and from edge nodes maintain the highest standards of security and resiliency. Many organizations, in an attempt to ensure that their edge remains secure and accessible, have chosen to offload their edge protection to “trusted” third parties, granting unfettered access from the third party to the organization’s sensitive resources.
Edge devices are often deployed in, or adjacent to, degraded and untrustworthy (“dirty”) networks. It is imperative that organizations secure edge node devices, the communication to and from devices and nodes, and stabilize degraded (jittery) network connections to ensure that critical data is safely received.
Edge Devices Pose Signifcant Risks
Edge devices act as the intermediate between secured networks and “dirty” external networks, such as public internet infrastructure in hostile environments. This unique position makes the edge susceptible and potentially vulnerable to attacks from hostile nation-states and actors and can make system updates – including those that close severe vulnerabilities – difficult or impossible.
These realities challenge established notions of perimeter defense, making it clear that legacy firewalls, static rules, and complex overlays (like service meshes) fail to keep pace with true container-driven operations. Container security must be as dynamic and granular as the environments it protects.
Traditionally, edge nodes must have routable IP addresses. Unfortunately, these public IP addresses become the focal point for attacks due to their public reachability. Next-generation network security and access technology can make edge nodes invisible and immune from inbound attacks, stabilize the network, and allow safe, authorized access for system maintenance.
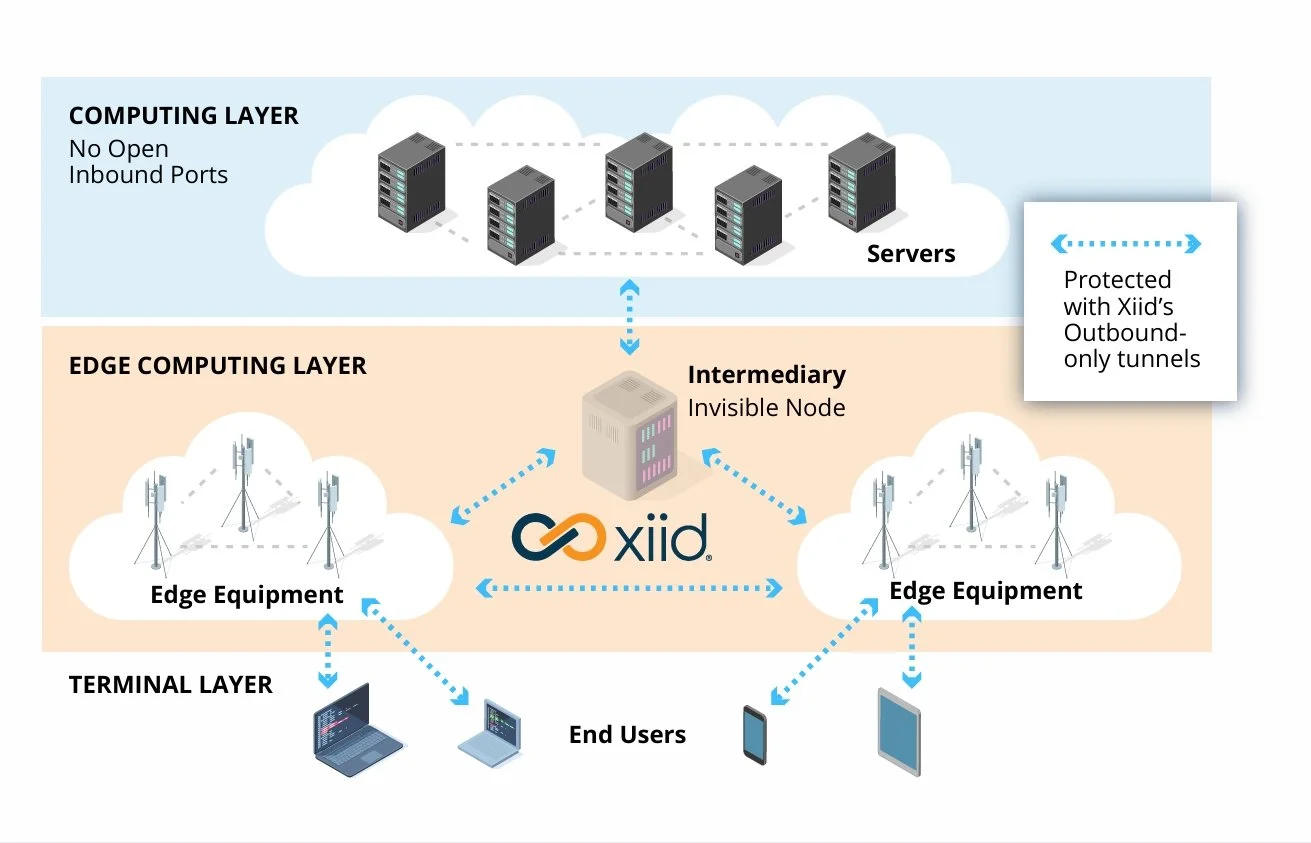
Xiid’s SealedTunnel™ Secures and Hides Edge Nodes
Xiid’s SealedTunnel™ makes edge nodes invisible by leveraging triple-encrypted, outbound-only communication that allows them to be non-addressable with no public IP address or open inbound ports required. This same secure communication can be used to patch the edge nodes and apply system updates. SealedTunnel also leverages packet buffering to ensure that critical information is never lost, even when the networking connection spontaneously drops.
Because Xiid’s outer encryption layer uses TLS 1.3 over HTTPS, SealedTunnel connections are hidden among other generic HTTPS traffic across the “dirty” internet, disguised as a normal connection to a web server.
Xiid’s SealedTunnel can also be leveraged to ofoad data from edge nodes to secure locations without either endpoint (edge device or secure ofsite device) knowing each other’s locations – ensuring the security and integrity of corporate networks.
Xiid manages outbound-only connections to edge nodes from devices at the terminal layer and from the computing layer. The SealedTunnel™ allows for devices in all three layers to close all inbound ports, making them invisible to unauthorized devices and from the external network.