Tactical Communications over Unstable Networks for UAVs, Sensors, and IoT Devices
Tactical Devices on Hostile Networks are Hard to Secure
Tactical deployments of digital equipment are critical on the modern battlefeld. Physically securing tactical devices and sensitive communication to and from them (e.g., information ofoading, instruction uploading, maintenance, etc.) are key concerns.
Tactical edge devices are often deployed in hostile territory and may sometimes utilize degraded and untrustworthy “dirty” networks. It is imperative to leverage robust, “Secure-by-Design” technology to simplify, stabilize, and enhance the security of in-theater devices and their communication channels.
Unstable Networks Pose Additional Communication Challenges
Tactical devices such as drones, UAV access points, and other IoT sensors sometimes rely on degraded communications over 5G or satellite-based networks and are subject to drops in network connectivity which could result in the loss of critical battlefeld information. Devices are also subject to attacks from nation states, malicious actors, and other cyber threats. These attacks include surveillance of sensitive information collected by devices, man-in-the-middle attacks, and denial-of-service attacks blocking data from reaching its destination.
Xiid’s SealedTunnel™ Stabilizes and Secures Communication in Hostile Environments
Xiid’s SealedTunnel makes tactical devices reachable for authorized use but invisible and non-addressable by threat actors with bi-directional, triple-encrypted, outbound-only communication that allows for all inbound network ports to be closed.
SealedTunnel also leverages packet buffering to ensure that mission-critical information is never lost, even when the network connection spontaneously drops. Additionally, because Xiid’s outer encryption layer uses TLS 1.3 over HTTPS, SealedTunnel connections are hidden among other generic HTTPS trafc across the “dirty” internet and disguised as a normal connection to a web server.
For example, while a hostile actor may be able to physically see a drone, they can neither access the drone nor intercept its data transmissions. Additionally, since Xiid’s Zero Knowledge Networking platform never stores or requires any information regarding the ultimate endpoint it talks to, if a drone is physically compromised, zero information can be recovered on the true destination that data was sent to or from.
Xiid’s SealedTunnel software is extremely lightweight, allowing it to work efficiently on small devices such as the Raspberry Pi or NVIDIA Jetson Nano.
Drone/UAV Example
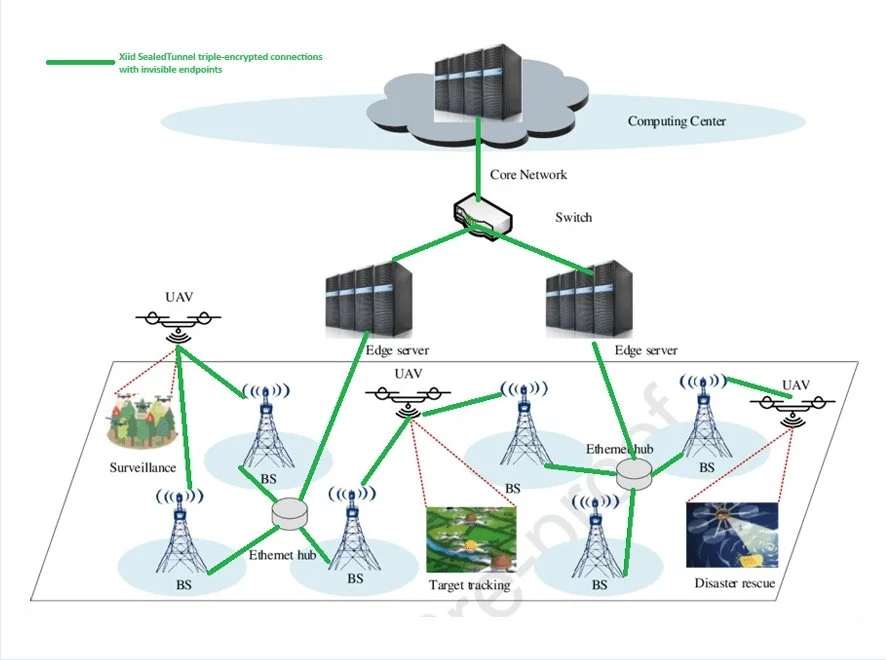
This diagram outlines multiple UAV use cases, with green lines indicating network connections secured by Xiid’s SealedTunnel™ product. Each of the endpoints connected by green lines supports unidirectional and bidirectional communication. Due to the lack of open inbound ports required on endpoints, each endpoint’s network connections are invisible to external threat actors and every green line is disguised as standard HTTPS web traffic.