Application-level security for any transport, vendor, or cloud.
Simplify your network, lower operational costs.
How Terniion protects your environment
Terniion exceeds Zero Trust by exposing nothing and preventing everything—without forcing you into a single vendor, cloud, or network architecture.
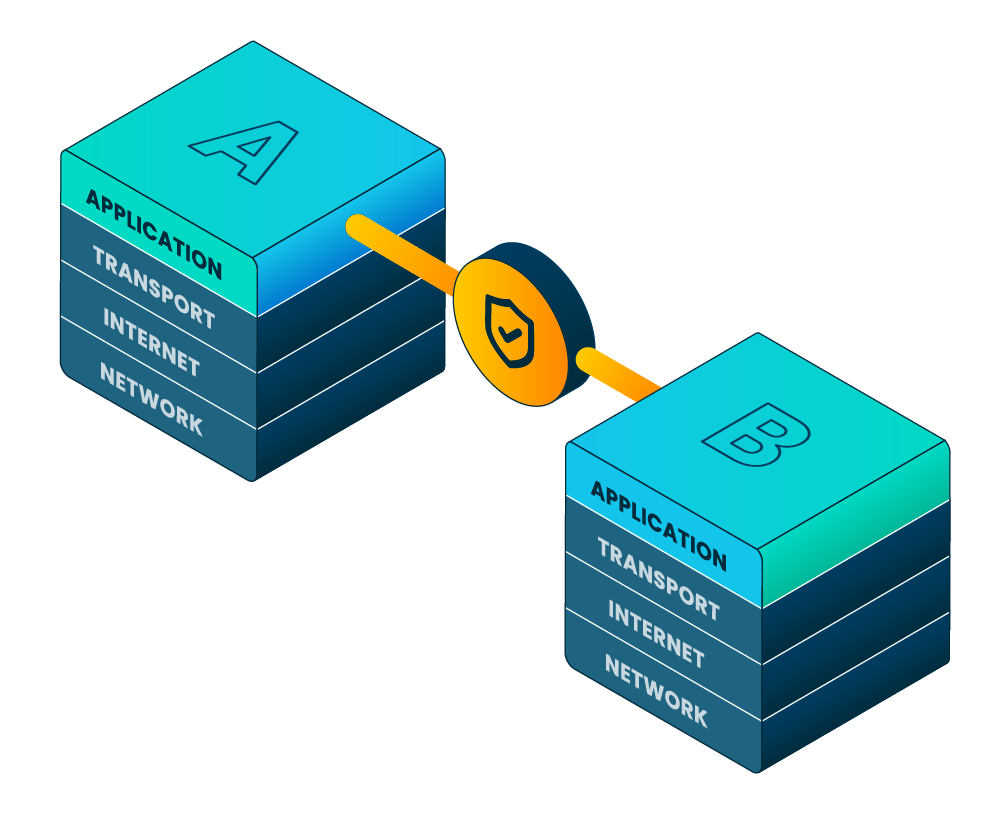
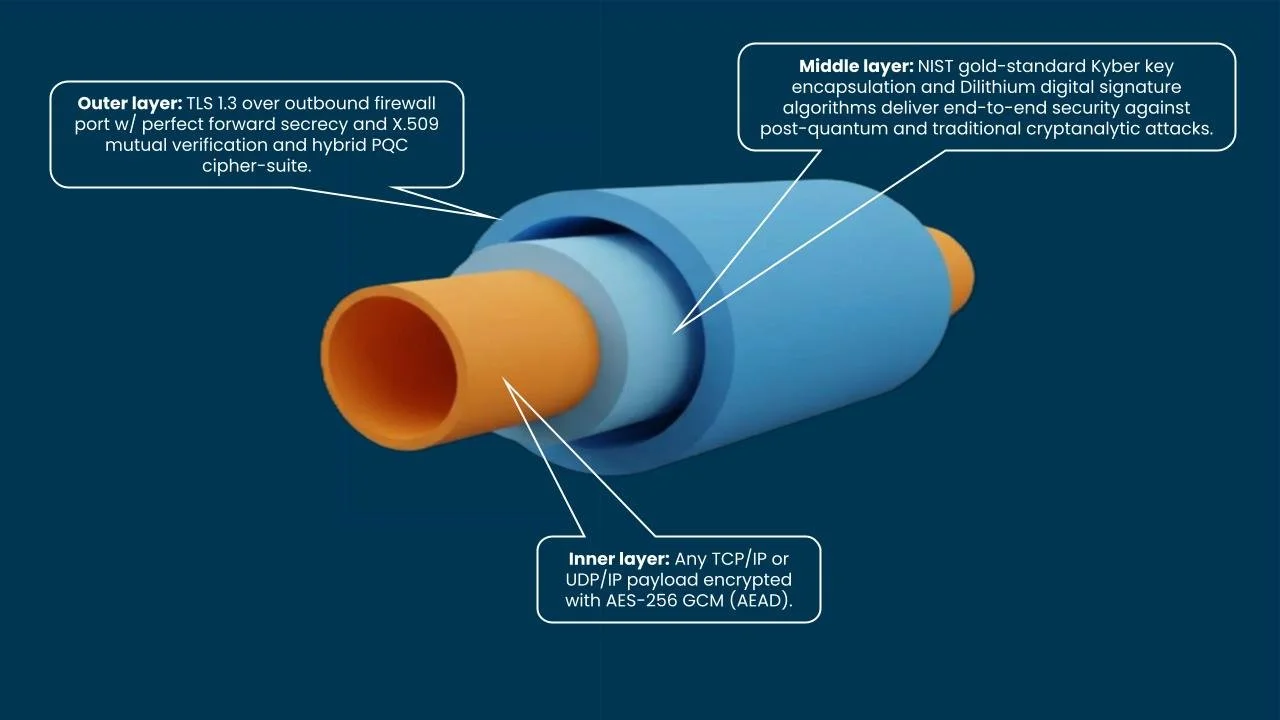
It wraps existing applications, pipelines, and services in triple-layer, quantum-resistant encryption, while outbound-only connectivity makes critical resources non-routable and out-of-range to attackers.
Any transport, any vendor: Secure application-level connectivity across mixed clouds, data centers, SaaS, and legacy infrastructure without changing underlying networks.
Process-level microsegmentation: Bind access to specific processes, not just IPs or subnets, so a compromise can’t pivot across your environment.
Government-grade assurance: DoD IL5 Authority to Operate and Air Force–validated near-invisibility give you confidence in high-stakes, regulated workloads.
What is Terniion?
Terniion is a platform that moves your network security beyond detect-and-respond. Instead of adding more locks to a building, it removes all doors and windows, eliminating exposure and making your entire infrastructure unreachable by attackers. No inbound connections, no public IP addresses. Instead, process-to-process tunnels create isolated, protected paths for every connection, stopping lateral movement before it starts. The first component of Terniion is SealedTunnel.
SealedTunnel
Our tunneling solution provides secure access to resources across any network, closing the door on vulnerabilities and security risks.
Aclave Authentication Management System
Delivering a highly secure Single Sign On (SSO) and resilient, outbound-only, credential-less one-time-code authentication solution.
Xiid’s Authentication Management solution is a fully credential-less authentication process for both on-premises and cloud-based users.
The XOTC™ Authenticator and Single Sign-On (SSO) Portal eliminate the risk of credential theft by using Zero Knowledge Proofs and unique one-time codes for each login session.
Patented Smart Hybrid Protocols (SHyPs), an application-aware layer, prevent the possibility of code injection.
Virtualized Trust Relationships make integrating multi-domain environments (trees and forests) easy and seamless.
Aclave IAM also offers the advantage of easily integrating into existing environments, providing added power to your current investments without requiring rip-and-replace.
The Xiid RDP Agent secures passwords on machines and integrates with Xiid’s SSO Portals so that employees never need to remember a username or password.