Securing Dynamic Containerized Environments
Xiid SealedTunnel™ 4.0 Case Study
Introduction
Organizations in a variety of industries are switching from static legacy systems to dynamic, containerized architectures driven by CI/CD pipelines and Kubernetes. Unprecedented speed, scalability, and development velocity are brought about by this evolution, but it also opens up new attack vectors and reveals serious security flaws that conventional network and perimeter-based controls cannot fix.
Businesses must deal with the distinct and quickly changing security challenges posed by containerized, ephemeral, and distributed microservice workloads as they embrace the agility of cloud-native infrastructures. Xiid SealedTunnel 4.0 is a radically novel method designed specifically to protect these contemporary settings at the rate at which they change.
Industry Challenge: The Modern Container Security Gap
Across sectors—whether finance, healthcare, manufacturing, or technology—operational environments are marked by:
Ephemeral Workloads: 70% of containers live less than 5 minutes, with attack windows often completing within 10 minutes 1
Constant Change & Scaling: Continuous deployments and updates introduce new workloads at breakneck speed, while auto-scaling sees containers rapidly spin up and down to meet demand.
IP Address Volatility: Containers are regularly restarted or moved, causing frequent IP changes that render static network policies and firewalls ineffective.
Orchestration & API Exposure: Control planes, such as Kubernetes APIs and registries, form high-value targets with elevated privileges and lateral movement risks.
These realities challenge established notions of perimeter defense, making it clear that legacy firewalls, static rules, and complex overlays (like service meshes) fail to keep pace with true container-driven operations. Container security must be as dynamic and granular as the environments it protects.
The Xiid Solution: Zero Knowledge Container Security with SealedTunnel™
Xiid SealedTunnel was engineered to directly address these pervasive industry issues through several core innovations:
Process-to-Process, Outbound-Only Security
By establishing process-level tunnels—instead of relying on IPs or hostnames—SealedTunnel ensures every containerized process maintains an immutable, isolated, and identifable security boundary, regardless of how underlying infrastructure or IP addresses change.
All connections are outbound-only and triple-encrypted with multiple layers of end-to-end encryption, meaning containers and hosts never expose inbound ports or data to middlemen or attackers. This outbound architecture eliminates exposed attack surfaces and signifcantly reduces the risk of lateral movement within the cloud or data center.
Quantum-Secure Triple Encryption
SealedTunnel augments defense-in-depth with three distinct layers of encryption:
TLS 1.3 for outer-layer transport security
Kyber KEM and Dilithium digital signatures for post-quantum resilience
AES-256-GCM AEAD as the inner core
This allows organizations to future-proof sensitive data and operations even as quantum computing threats evolve.
Automated, Profle-Driven Security with SealedTunnel Profles
SealedTunnel Profles make it possible to deploy fully-networked, pre-confgured, and securely isolated containers with no manual intervention. Standardized, template-based mappings and bindings mean security is consistent and immediate for new workloads, enabling seamless horizontal scaling without security bottlenecks or manual interventions.
Multi-Cloud, Multi-Pattern Support
With Kubernetes integration (including sidecar, daemonset, and gateway models), enterprises enjoy cloud-agnostic security that travels seamlessly across AWS, Azure, Google Cloud, on-premises, and edge deployments.
Use Cases Across the Modern Enterprise
Agile Microservices
Organizations supporting microservice architectures benefit from SealedTunnel’s process-to-process tunneling and microsegmentation, allowing secure horizontal scaling, without IP or firewall reconfiguration delays, and resilient, secure inter-service communication.
CI/CD and Software Supply Chain Security
As CI/CD pipelines become attack vectors, SealedTunnel delivers complete network isolation for build runners and code repositories. Outbound-only connections and zero required public IP exposure neutralize zero day attacks and emerging threats.
Machine Learning, AI, IoT, and Edge Workloads
From large model delivery to constrained edge devices, SealedTunnel ensures all data transfers are triple-encrypted, resilient to unreliable networks, and securely isolated regardless of the underlying compute platform.
Business Impact and ROI
Security Risk Reduction
• Drastically reduced attack surface: No open inbound ports and immutable process boundaries.
• Breach containment: Lateral movement is prevented at the process level—not just at the endpoint.
• Compliance readiness: Automated, robust encryption and access controls facilitate PCI DSS, HIPAA, and SOC 2 alignment.
Operational Effciency and Cost Optimization
• Streamlined deployment: Automated profile-driven configuration enables rapid environment provisioning, and continuous deployment.
• Elastic scalability: Security scales seamlessly with application loads, without creating network configuration-related chokepoints or delays.
• Toolchain consolidation: SealedTunnel replaces multiple legacy tools, reducing licensing and management overhead.
Proven Reliability
Xiid’s platform is feld-tested in hostile environments, penetration tested by the U.S. Air Force Research Laboratory, and has been granted an Authority to Operate by the U.S. Department of Defense, proving real-world resilience for critical and sensitive workloads.
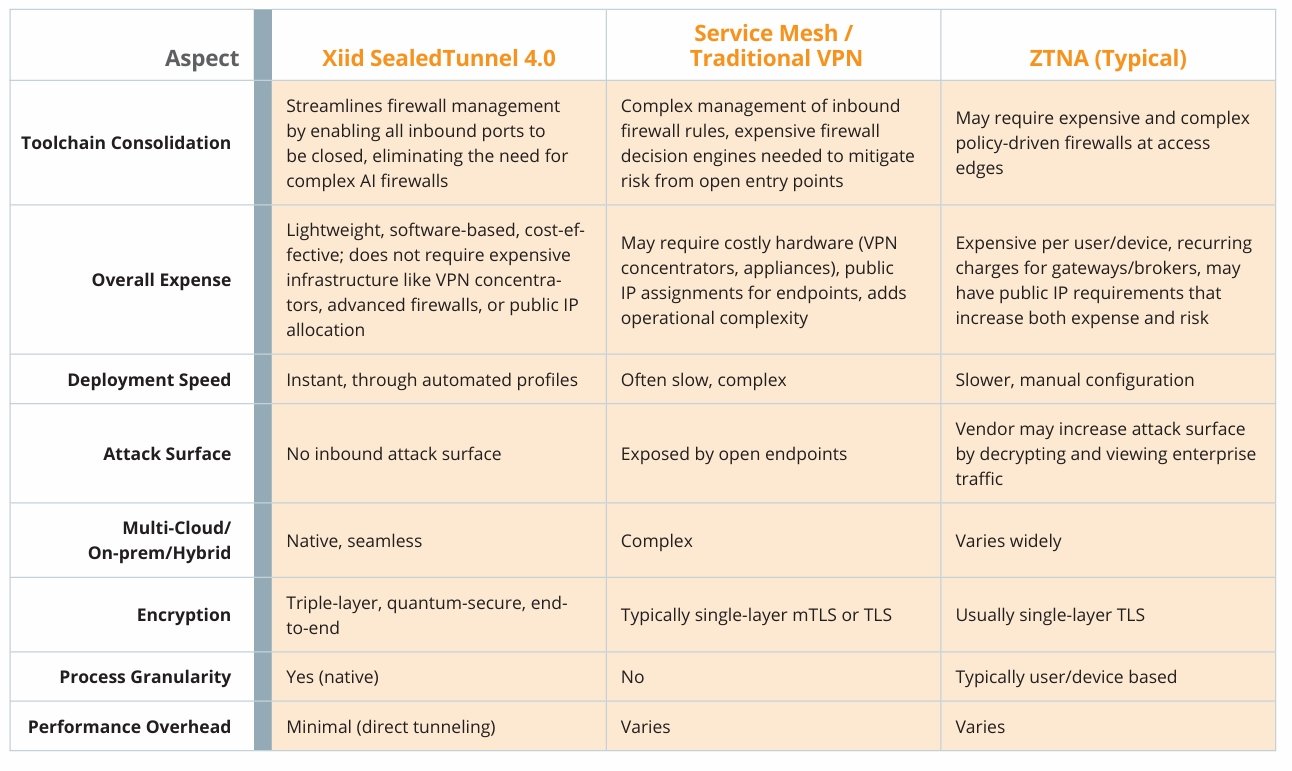
Comparative Assessment
Conclusion
Only the process-to-process, zero-knowledge, outbound-only SealedTunnel can keep pace with the operational realities of modern dynamic containerized architectures. Xiid SealedTunnel 4.0 provides the automation, quantum resilience, and integration needed to make security a force multiplier for DevSecOps—not a drag.
Organizations investing today in profle-driven, quantum-secure, process-isolated networking are well-positioned to thrive as the demand for speed, regulatory compliance, and security grows—across cloud, edge, and the inevitable quantum-powered future.