Zero Trust vs. Zero Knowledge: Why Not Both?
Zero Trust and Zero Knowledge sound similar, but they deliver radically different results. Zero Trust laid the foundations for “never trust, always verify,” to reduce risk through strict access controls, continuous monitoring, and identity-driven security. But most modern organizations now want safeguards that are both practical and truly future-ready; here comes Zero Knowledge.
Photo by Caspar Rubin on Unsplash
What is Zero Trust?
Zero Trust is a cybersecurity philosophy built on the idea that you “never trust, always verify”. Access to company resources is restricted to those who are authenticated and authorized, regardless of network location.
Typical features: Multifactor authentication, granular policy enforcement, continuous monitoring, network segmentation, and integration with identity providers.
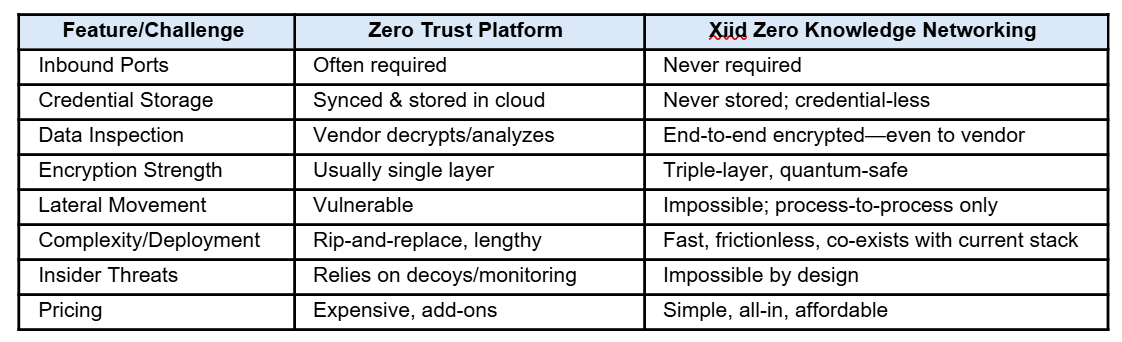
Zero Trust products often market process, policy, and AI-based threat analysis, but generally require federation of user identities, break-and-inspect of network traffic, and open inbound ports.
Zero Trust Challenges
Despite heaps of marketing, most “Zero Trust” platforms have three core weaknesses:
Open doors: Most solutions still require open inbound ports, leaving entry points for attackers and exposing assets to scanning and exploitation.
Third-party trust issues: Identity providers store and sync user credentials, which become honeypots for attackers, and yes, these providers do get breached.
Complexity: Deployments are slow, expensive, and often require significant network overhaul and management overhead, sometimes resulting in frustrated users who seek insecure workarounds.
What is Zero Knowledge Networking?
Zero Knowledge Networking builds on Zero Trust architecture, taking its principles further by eliminating credential exposure, closing inbound ports entirely, and preventing vendor data access, even in the event of a breach. Instead of requiring a complete overhaul or replacement, Zero Knowledge Networking is additive: it co-exists with and strengthens existing Zero Trust deployments, bringing quantum-resistant encryption and credential-less authentication to the party without breaking what’s already working.
Zero Knowledge Networking (ZKN) is a next-generation approach that shrinks the attack surface to near zero. It validates users and devices without ever storing credentials or sharing sensitive data. Even the provider is blind to network traffic, user identities, or resource locations.
Outbound-only connections: No inbound ports are ever opened. Systems become invisible to attackers—if the doors don’t exist, no attacker can knock.
Triple-layer, quantum-resistant encryption: Traffic is wrapped in three distinct encryption layers, including end-to-end, quantum-resistant algorithms. [Read More]
Credential-less authentication: Verification happens without credentials flowing over the internet (goodbye, phishing, and credential theft), using Zero Knowledge Proofs for future-proof validation.
No third-party trust required: Vendors never have access to your data or user identities. Your risk exposure is slashed even if the provider is compromised.
Zero Trust vs. Zero Knowledge
Zero Knowledge adds these properties to any Zero Trust framework to shrink the attack surface, and remove centralized credential stores, keeping data private at every step.
Next-gen Zero Trust: Zero Knowledge Networking as a Force Multiplier
Technical leaders and execs want security that’s both robust and practical. Next-gen Zero Trust means eliminating entry points, never storing credentials, and wrapping traffic in quantum-safe encryption that even the provider can’t see.
Xiid’s Zero Knowledge Networking is Secure by Design: No open ports, credential-less authentication, no data exposure, and it deploys in minutes, all without breaking your existing stack.
Risk reduction is retro; risk elimination is the future. IT leaders don’t need to choose between Zero Trust and Zero Knowledge; they can implement both for bulletproof, future-proof security. Zero Knowledge amplifies Zero Trust’s core value without introducing complexity, add-on pricing, or painful migrations. It simply makes secure networks smarter, safer, and quantum-ready.
TL;DR
Zero Trust built the walls—Zero Knowledge adds the force field. Together, they make enterprise security truly unreachable, unaddressable, and out-of-range for attackers.